Increasing information leakage incidents along with advancement of IT
With the advancement of IT in business, large amounts of digital information are frequently exchanged at businesses, between businesses, or between a company and an individual through networks. Global managements have advanced and their information is exchanged beyond national borders. The information includes technological information such as intellectual property, confidential business information and personal information. However, the so-called information leakage incidents, like confidential information leakage without any malicious intention, have been increasing. Once an incident occurs, it causes much trouble for business partners, and the company that caused the incident will also lose their faith and sometimes fall into a difficult situation in regard to the continuity of the company.
Enhancement of information security is a requirement of the times
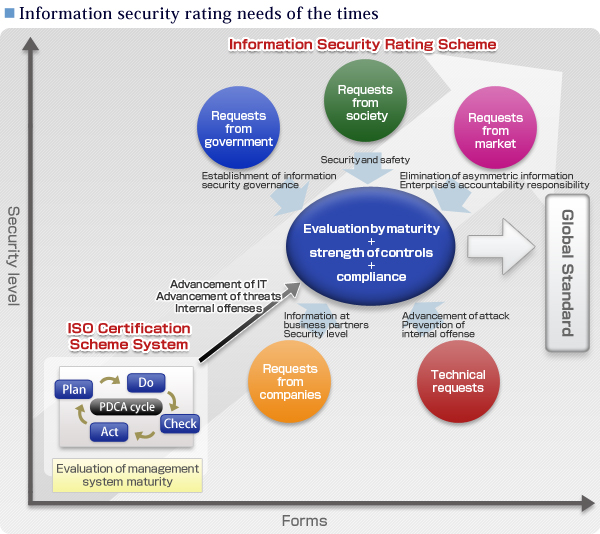
The theme of strengthening information security started to become prevalent in the 21st century. There are now social requests for safety and security, technical requests to prevent enhancing attacks and insider offenses, market requests to seek accountability from enterprises and government requests to ask for establishment of information security governance. These are all needs of the times.
Important management challenge
It is a crucial management subject for commercial enterprises to suitably manage substantial amounts of information. Many companies have started efforts to strengthen information security, but it is difficult to satisfy their business partners. This is partially because there is no easy-to-understand measurement for information security evaluation.
CSR activities for information security vs. environment
Companies that focus on "environment" and "information security" from the standpoint of CSR (corporate social responsibility) have been increasing, with certification schemes for "environment" and "information security" set by International Organization for Standardization (ISO). The companies that have acquired such certification announce it officially and use it as an advertisement. As for the environment, enterprises can build up their "environmentally friendly company" image through visible activities such as "call for recycling of products," "use of recycled materials," and "cooperation for tree planting by corporate members." For information security, however, there are no ideas for appealing through external activities.
Expectation to new third-party evaluation
As for information security, the "fair evaluation by a third party" is mandatory. To prevent advancing threats from the outside and information leakage from the inside, the new third-party evaluation scheme is required, besides the conventional certification scheme (ISO 27001) of evaluating management level, for fair and detailed ranking. To answer this expectation, "information security rating" was developed.
Highly advanced evaluation method
Information security has many problems, from manipulation of websites, hardware and software troubles to information leakage. ISMS (Information Security Management System) is the way to address these problems as organizational management as well as by applying technology controls to them. Certification by ISO 27001 evaluates whether the PDCA cycle - Plan (Establishing the concrete plan and objectives), Do (introduction and operation of measures), Check (monitor/review of implementation results) and Act (improvement/action)-is continuously working. On the other hand, "Information Security Rating" ranks the security level. Specifically, the ranking is evaluated from standpoints such as maturity of the management system, strength of measures against threats and the state of legal compliance, using the highest level of AAA among 17-level symbols. As for the evaluation criteria (Criteria), the highly advanced evaluation method has been prepared in line with actual situations considering evaluation standards for information security controls at some leading companies and experience in rating creditworthiness etc. in other markets.